
The Need for Secure Time
We all have a general idea about what it means to be secure.
If you boil it down, security relies on meeting three key elements: confidentiality, integrity, and availability.
Securing data is the focus of a multi-trillion dollar cybersecurity industry and the push towards a zero trust architecture.
But what about securing time?
Considering that all networks, financial transactions, and power grids need a common time reference, and a widespread disruption of that time source would be catastrophic.
Confidentiality isn’t a concern; after all, you want everyone to know the time.
But availability – having access to that time reference – and integrity - being assured the time is correct – are very important.
For most commercial users, this time reference is sourced via satellite through RF signals that can be easily jammed (removing integrity) and spoofed (removing authentication).
Fortunately, authentication concerns can be addressed through quantum communications.
Quantum communication systems that manipulate the quantum properties of photons were developed for the secure distribution of encryption keys, known as quantum key distribution (QKD).
The hardware and some of the underlining security protocols developed for QKD can also be applied for secure time distribution, effectively creating a trusted and authenticated time reference (see below).
This opens the door to a whole new paradigm for a future secure time network.
Last Week's Theme: Security vs. Resilience, and Why You Need Both
- Check out our presentations for:
- The Space Foundation Global Alliance Webinar and Speaker Series interview “Quantum Optical Communications as a Replacement for GPS.” Space Foundation provides “a gateway to education, information and collaboration for space exploration and space-inspired industries that define the global space ecosystem.”
- Foundation for the Future podcast. The Foundation for the Future is “dedicated to advancing the space economy by developing critical infrastructure to enable it, investment tools to finance it, and a workforce to power it.”
- QED-C Quantum Marketplace presentation: “Network Security Post Quantum.” The Quantum Economic Development Consortium (QED-C) was formed by US National Quantum Initiative Act to “enable and grow the quantum industry.”
- Completed our Q1 2023 Board of Directors meeting.
- Developing new proposals, IP, and hardware.
- Planning for presentations (supporting LSU) at the Quantum 2.0 Conference in two weeks, a Time Appliances Project session in July, and our next Investor Session (details to be announced soon!).
- Some analysts believe that China would act early to disrupt GPS and other satellites in case of a conflict, as described in a set of wargames that claim that “the threat of an attack on GPS could be enough to deter America from defending Taiwan.”
- It’s not just MEO satellites like GPS that are getting jammed in Ukraine – Russia is also jamming LEO satellites like Starlink.
- The director of the US National Coordination Office for Space-Based PNT highlighted the need for a commercial solution to augment GPS: “The U.S. has long held the position that high-accuracy, precise point positioning services should be provided by commercial services...the commercial market is best suited to adapt to those changing customer needs and provide the best product.”
- Hackers tied to China were reported to have compromised critical U.S. cyber infrastructure, according to Microsoft and a National Security Agency bulletin.
- The National Geospatial-Intelligence Agency is developing a Lunar Reference Frame as “a lunar geodetic system that will guide future visitors around the moon’s surface as accurately and safely as GPS does on Earth.”
- Two major quantum initiatives were recently announced: Germany released a 3B Euro national quantum plan “Handlungskonzept Quantentechnologien” and Australia announced a National Quantum Strategy.
- It has been reported that the increase in solar storms is disrupting GPS and satellite communications, and could even impact the satellites themselves. Now there is a new concern: volcanoes. The recent Tonga volcano caused plasma bubbles in the ionosphere that “interfered with satellite communications.”
- European Navigation Conference, May 31 - June 2, Noordwijk, The Netherlands
- Quantum 2.0 Conference, June 18 - 22, Denver, CO
- Q4I, June 27 – 29, Rome, New York
- Small Satellite, August 5 – 10, Logan, Utah
- Euroconsult, September 11 – 15, Paris, France
- APSCC, October 10 – 12, KL, Malaysia
- ITSF, Oct 30 – Nov 2, Antwerp, Belgium
- UK National Quantum Technologies Showcase 2023, Nov 2, London, UK
- SLUSH, Nov 30 – Dec 1, Helsinki, Finland
Secure Time through Quantum Communications
Time distribution networks rely on “transferring reference clock synchronization from one point to another, often over long distances.”
Over global distances this is achieved via RF signals from a global navigation satellite systems like GPS (check out this site for a good explanation of how these systems work).
The satellite clock provides the time reference that is sent to the receiver via a RF signal.
This signal contains a pseudorandom code (sequence of ones and zeros) that is also known by the receiver.
The offset between the satellite code and the receiver code is then used to calculate the difference between the receiver and satellite clocks (or, conversely, the distance between the receiver and satellite using the speed of light).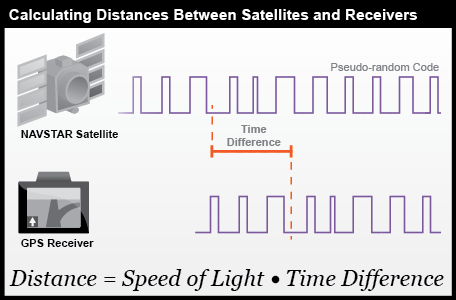
Credit: Department of Geography, The Pennsylvania State University
The problem: this RF one-way time transfer design is fundamentally insecure.
An adversary that wants to spoof the signal has two methods at their disposal:
- If they know the pseudorandom code, they can create their own signal.
- They intercept the original signal and modify it or re-transmit it with time delay.
But time transfer with entangled photons eliminates these security loopholes:
- By replacing the pseudorandom code with random entangled photons, thereby eliminating the possibility that an adversary would be able to create their own signal.
- By eliminating the ability to measure and re-transmit the quantum signal due to the no-cloning theorem.
This eliminates concerns about the authentication of the time reference.
The integrity of the time reference is addressed by building a resilient network.
To learn more, please email us or schedule a meeting here.

